DORA compliance software
With cybreg software, you can easily implement ICT risk management and meet all the requirements of DORA.
- Internal regulations, incident management, risk catalogue, roles and responsibilities
- Generation of mandatory reports in accordance with CNB requirements
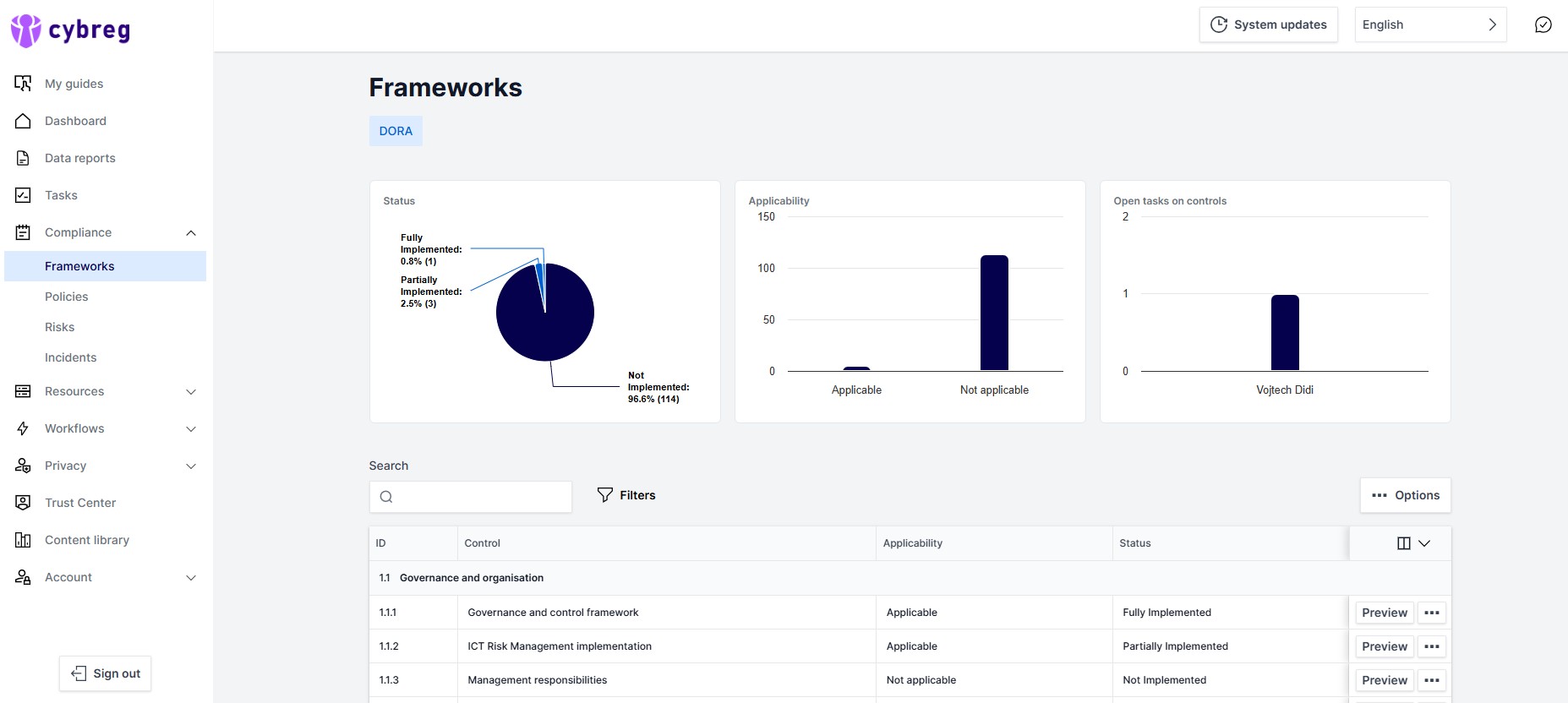
DORA implementation
The cybreg software includes a wizard that guides you through the entire process to ensure the implementation of DORA requirements. Dedicated legal and regulatory experts will help you create customised internal regulations and processes, including links to information assets, ICT assets, specific activities and other functionality.With cybreg, you get key data and a comprehensive framework for ensuring DORA compliance.
Management of information and ICT assets
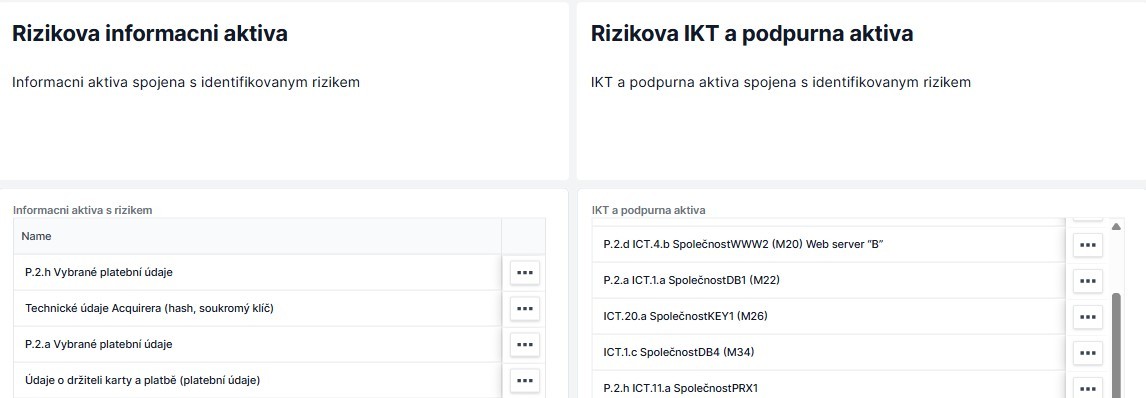
The cybreg software includes a catalogue of all information assets and ICT assets. It allows to store and display information about such assets and the persons responsible for the management of each asset. With cybreg software, you get the possibility to identify all processes linked to information and ICT assets, as well as to monitor the physical or digital security of these assets.
ICT risk management
The cybreg software will ensure the management and maintenance of the risk catalogue in accordance with DORA, including risk mapping and calculation of the resulting risk score in terms of their probability and impact. The software includes a flow chart providing a holistic and clear view of risks. The software also allows for seamless linkage with other elements such as your business activities, information assets and ICT assets.
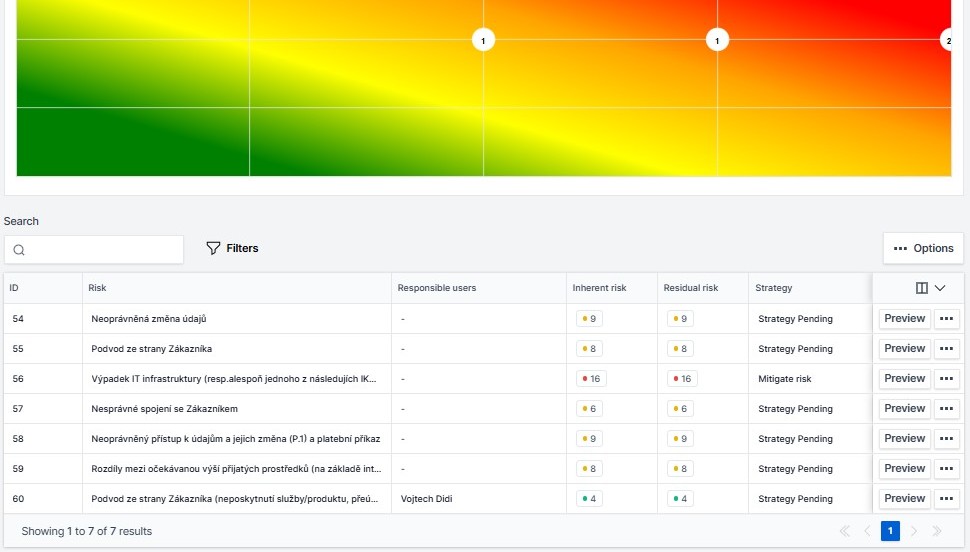
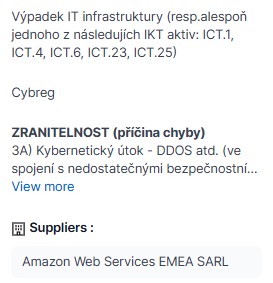
Managing risks associated with third parties
The cybreg ICT risk management software enables the management and control of risks associated with third-party ICT service providers. In particular, it is the regulatory management of contracts concluded with third-party ICT service providers and ensuring the content of such contracts in accordance with DORA. The software also provides the possibility to automate the process of monitoring and auditing the activities of a third party ICT service provider as required by DORA for such monitoring or auditing.
Questionnaires for the selection of third-party ICT service providers
The cybreg software will generate questionnaires for you to send to third-party ICT service provider candidates. The questionnaires contain all the necessary information that you will consider when selecting third party ICT service providers and will ensure that all the questions are covered so that the candidate can be selected in accordance with the DORA requirements.

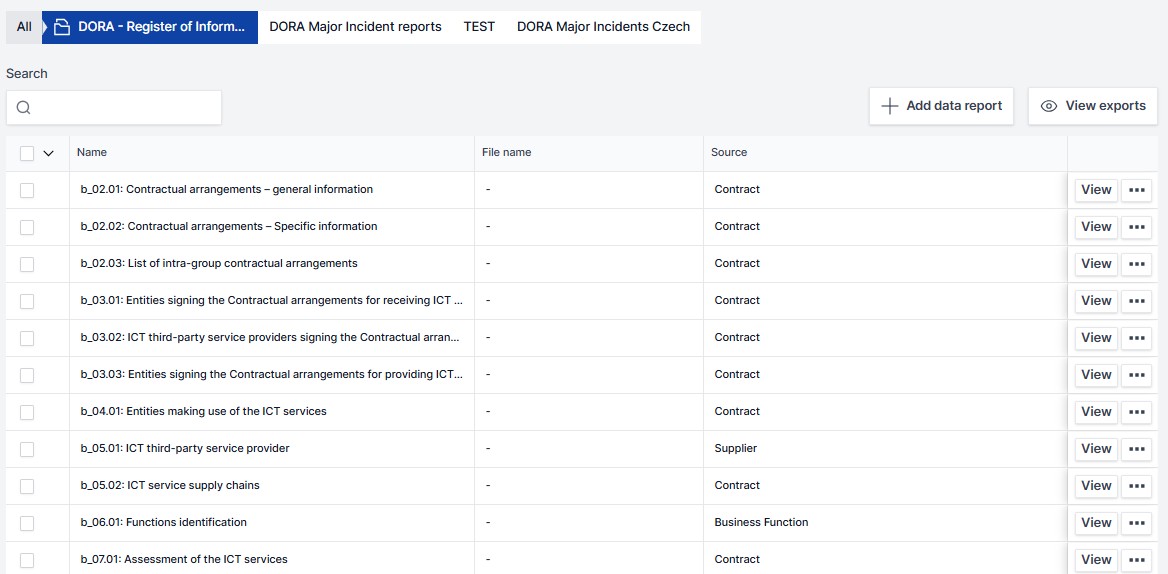
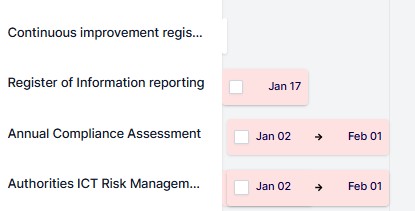
Register of information
The cybreg software comprehensively and clearly manages the record of information about third-party ICT service providers and the services they supply to you in the information register. The information register follows the format and scope prescribed for such a register under DORA. The cybreg software manages the information register so that it can be conveniently submitted to the CNB with all the necessary information at any time upon request.
Incident Management
The cybreg software ensures the management and generation of the necessary documentation for incident management in case of incidents according to DORA requirements.Incident management management includes detailed linkages with information assets, ICT assets, processes, risks and other elements. The individual steps can be automated. When an incident occurs, the software will ensure that the relevant reports are generated for submission to the CNB.
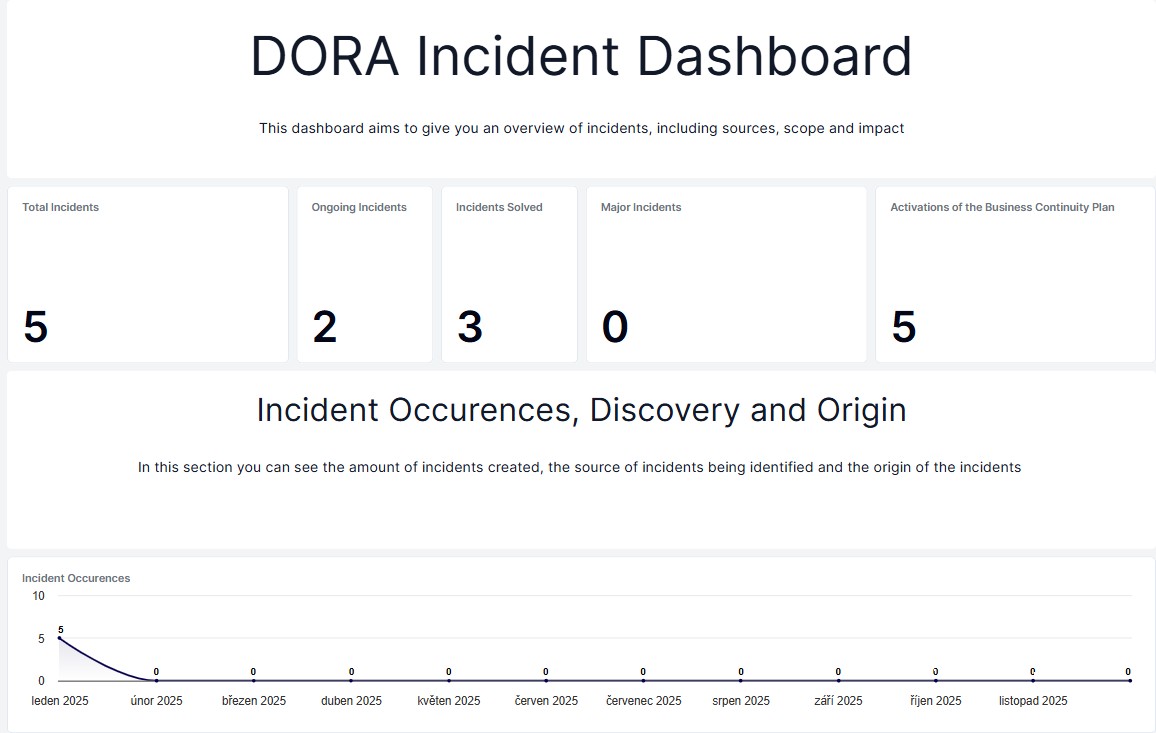
DORA reporting to the CNB
The cybreg software enables easy generation of all reports submitted to the CNB in the DORA mode, with the prescribed content, so that they can be submitted in the format required by the CNB.
Periodic reports
The cybreg software ensures the management and generation of the necessary documentation for incident management in case of incidents according to DORA requirements.Incident management management includes detailed linkages with information assets, ICT assets, processes, risks and other elements. The individual steps can be automated. When an incident occurs, the software will ensure that the relevant reports are generated for submission to the CNB.